PROJECTS

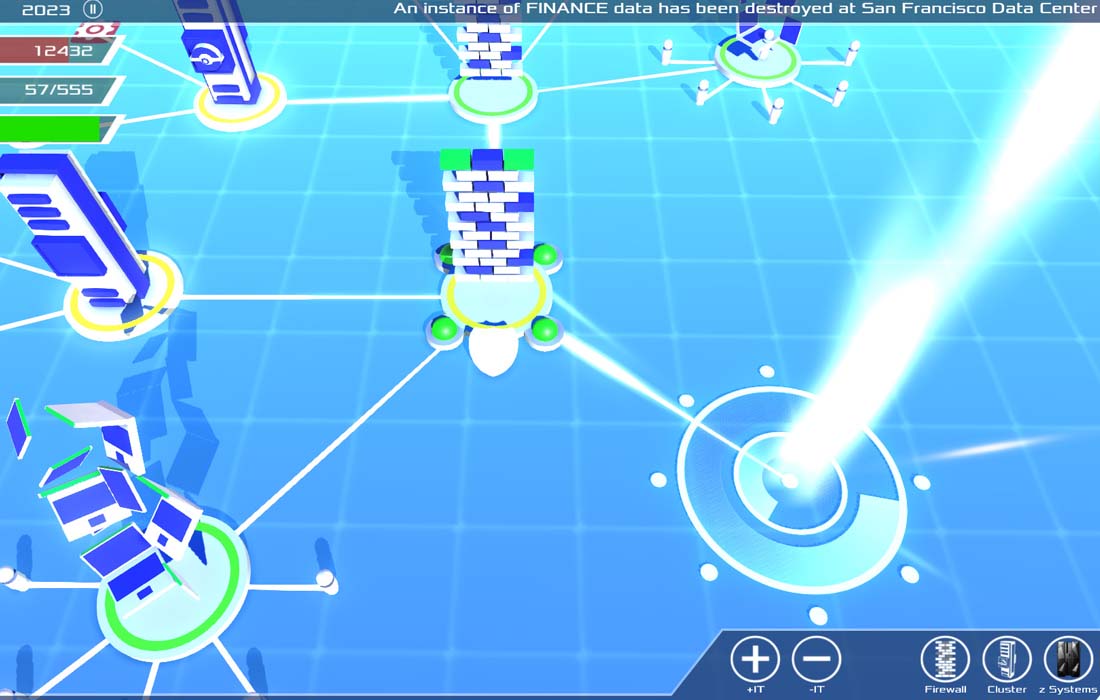
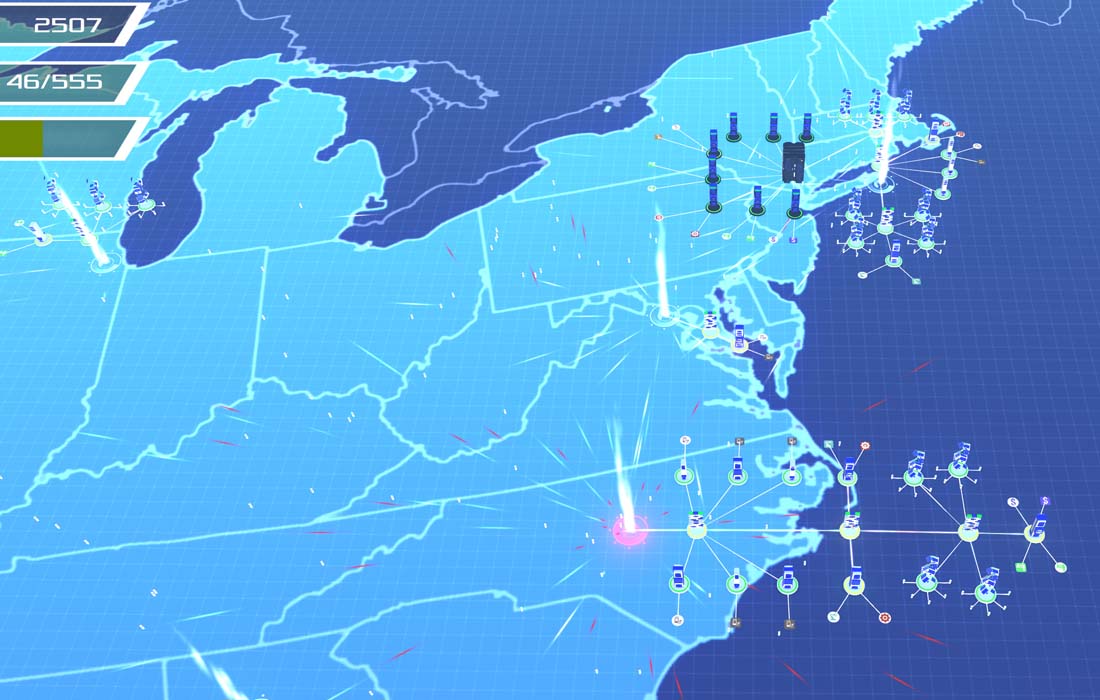
Cyber Threat Defender is based on the Cyber Security Layers simulation model, but tuned for a wide audience for marketing, communication, and training. Scenarios can be played out on mobile, web, and tablet platforms. Users can quickly test the comparative value of products, services, and configurations. Quickly evaluate the risks that IT systems are subjected to while navigating specific infrastructure challenges like acquisitions, rapid expansion, block chain adoption, and re-architecture. Integrate with cloud services, like IBM Bluemix, to see your IT infrastructure directly in the game. Or evaluate the benefits of an IBM z Systems Mainframe on your organization.
When your first-line defenses fail, will your entire organization be resilient?

Achron, launched in August of 2011, is the world’s first meta-time strategy game, a real-time strategy game where all players can travel through time. You can jump around the timeline, send your forces back in time, and undo ruses, and create grandfather paradoxes. Gamespot awarded it the 2011 Best Original Game Mechanic, Editor’s Choice Award.
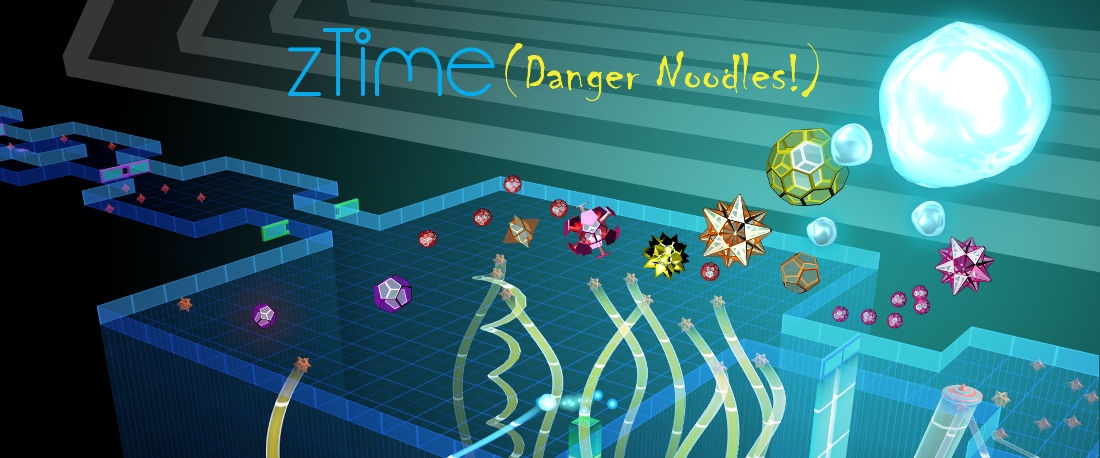
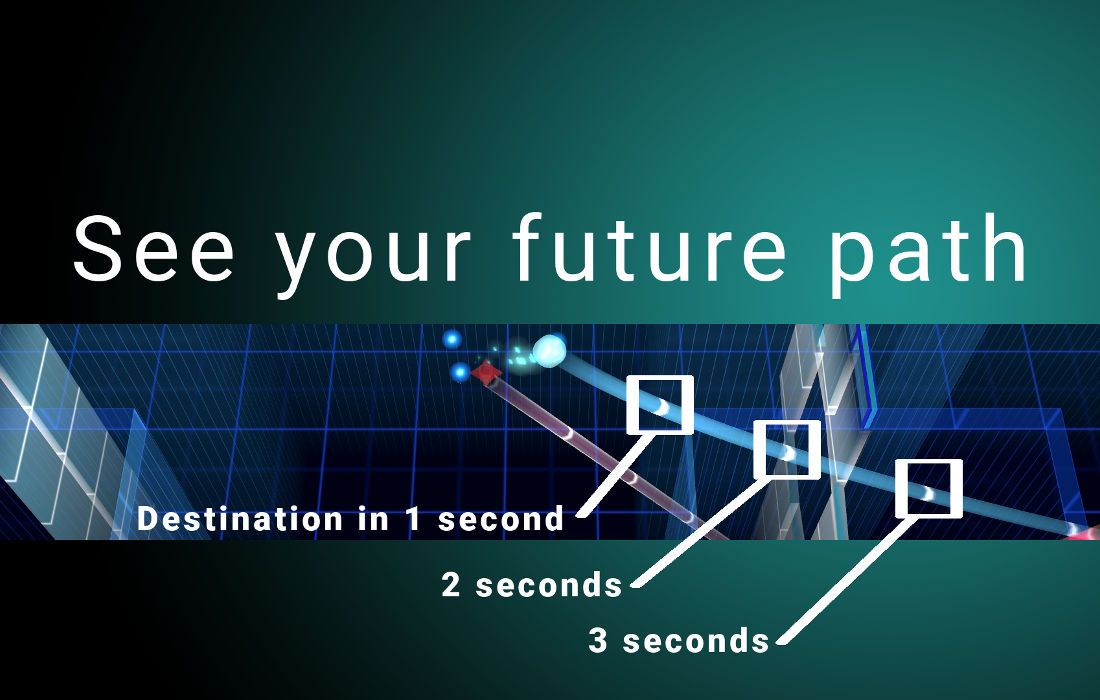
zTime (Danger Noodles!), coming in 2017, creates a visualization of the passage of time, drawing and updating the future paths and collisions of the player and environment objects. Having visual confirmation and certainty of future interactions which otherwise would rely on intuition gives players a feeling of having precognition and the ability to find windows of opportunity in seemingly impossible situations.
– vrgamesfor

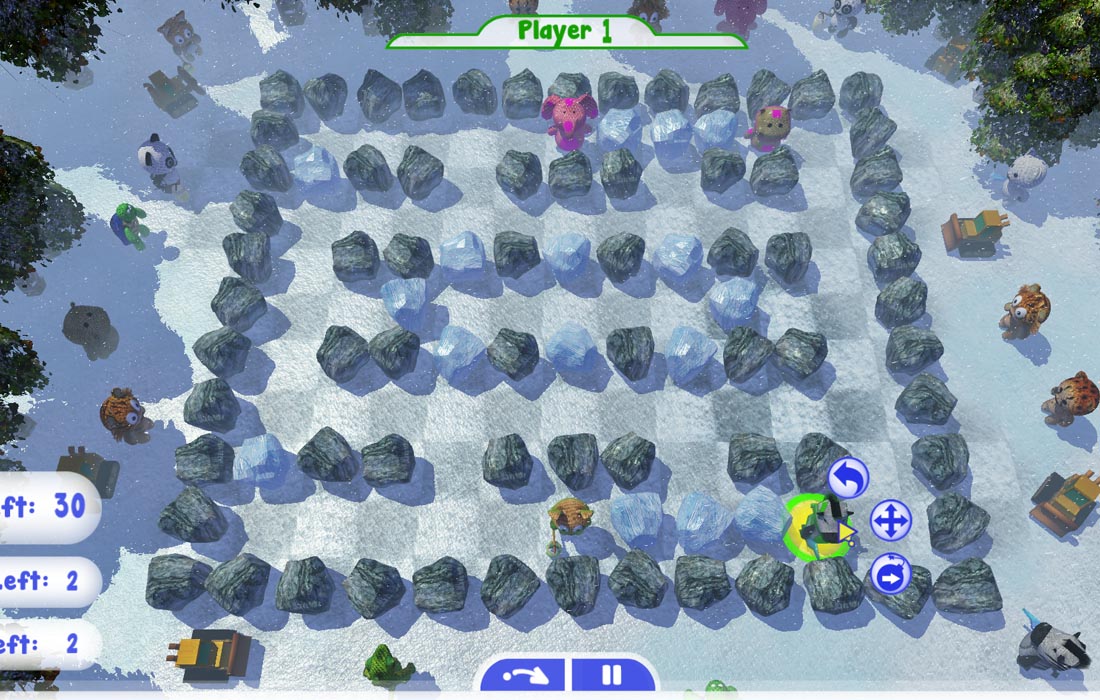
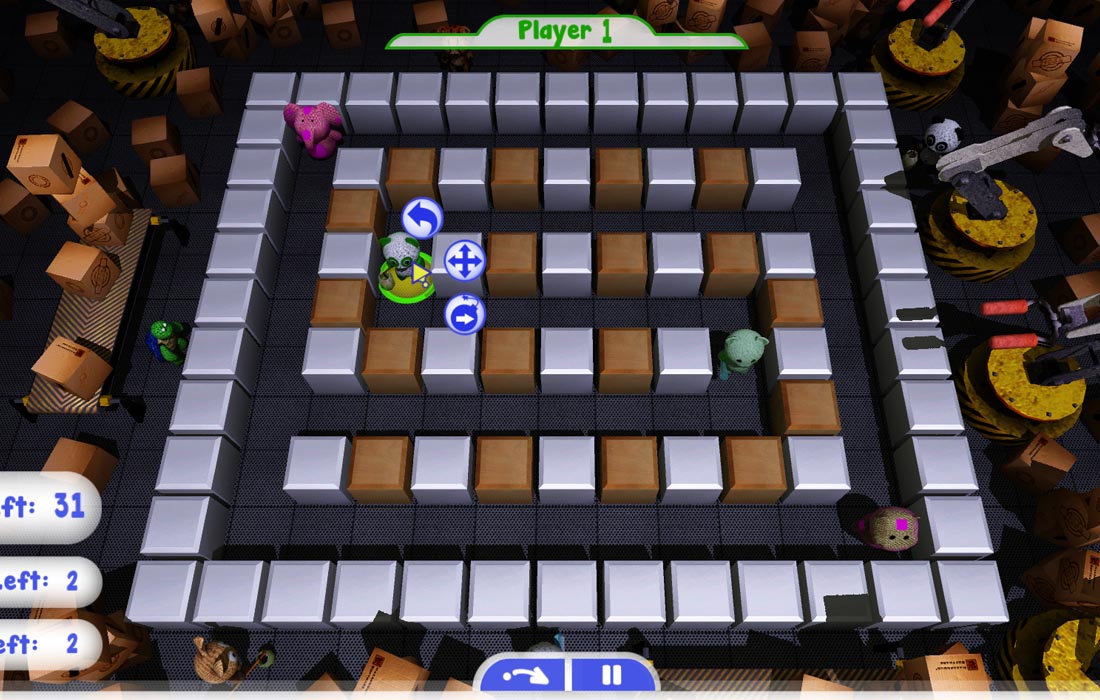
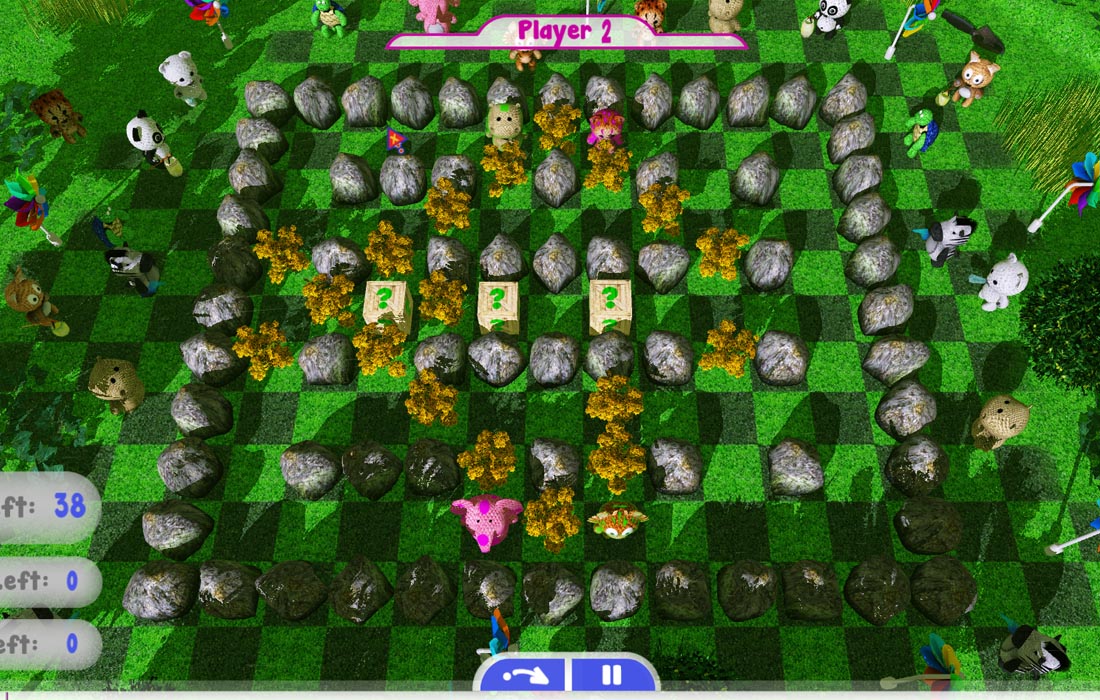
He who has the most toys wins! Challenge your game skills through a combination of playfulness, strategy and time manipulation. Plosh Time Bomb incorporates the Hazardous Software® Resequence Engine™ to provide time manipulation gameplay. Challenge your way of thinking about time against a friend or the AI. Plosh Time Bomb turns fast-paced crate-and-bomb game mechanics into a strategic turn-based game. It is a magical combat strategy game in which you play as Plosh animal rag-dolls, maneuvering through a maze of blocks while planting bombs to clear paths, destroy opponents, and paint-bomb your color everywhere.

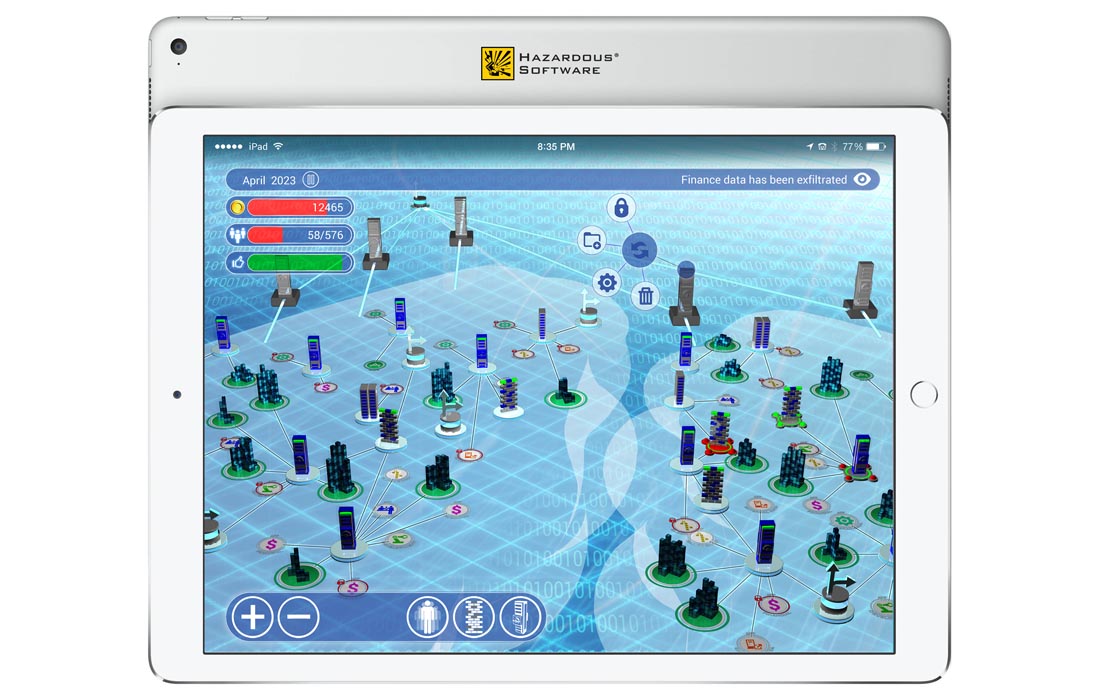
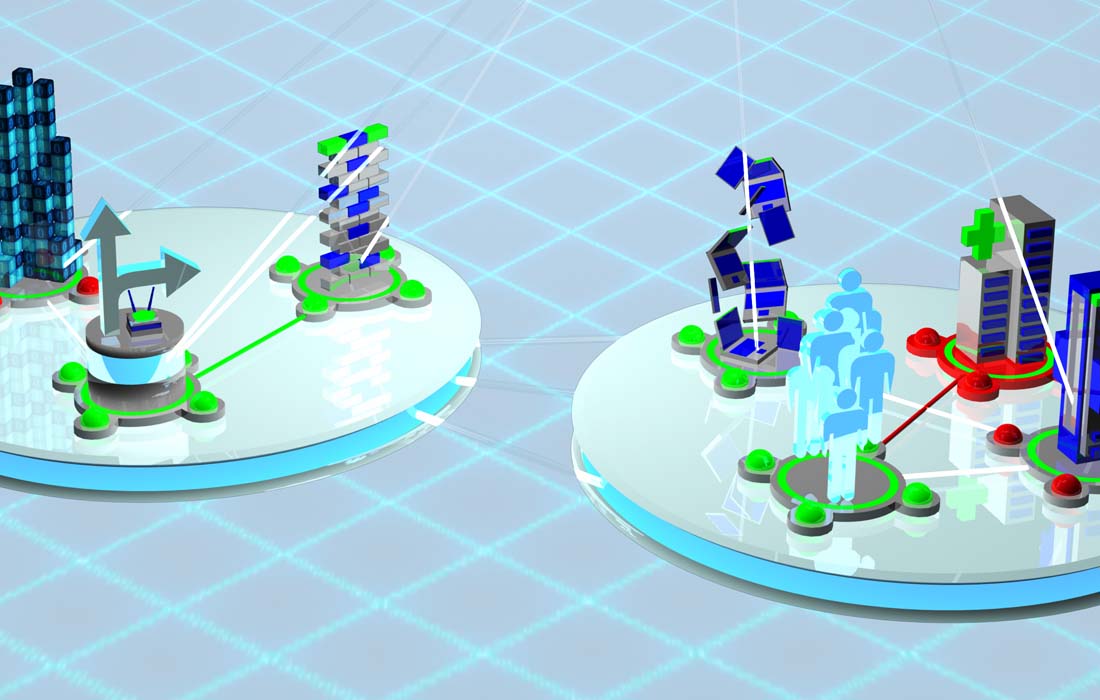
Cyber Security Layers is a serious game environment where you explore your strategic options surrounding the threats to your organization. By testing systems, knowledge, and policies in a simulated environment of heightened risk, players optimize their knowledge and approach to managing and balancing a variety of common information security challenges.
For more information on Cyber Security Layers, please contact info@www.hazardoussoftware.com.
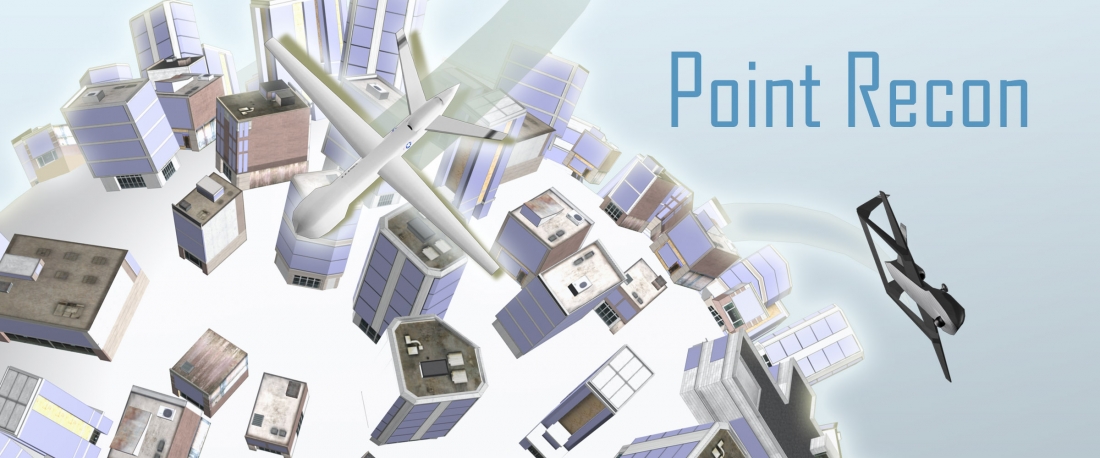
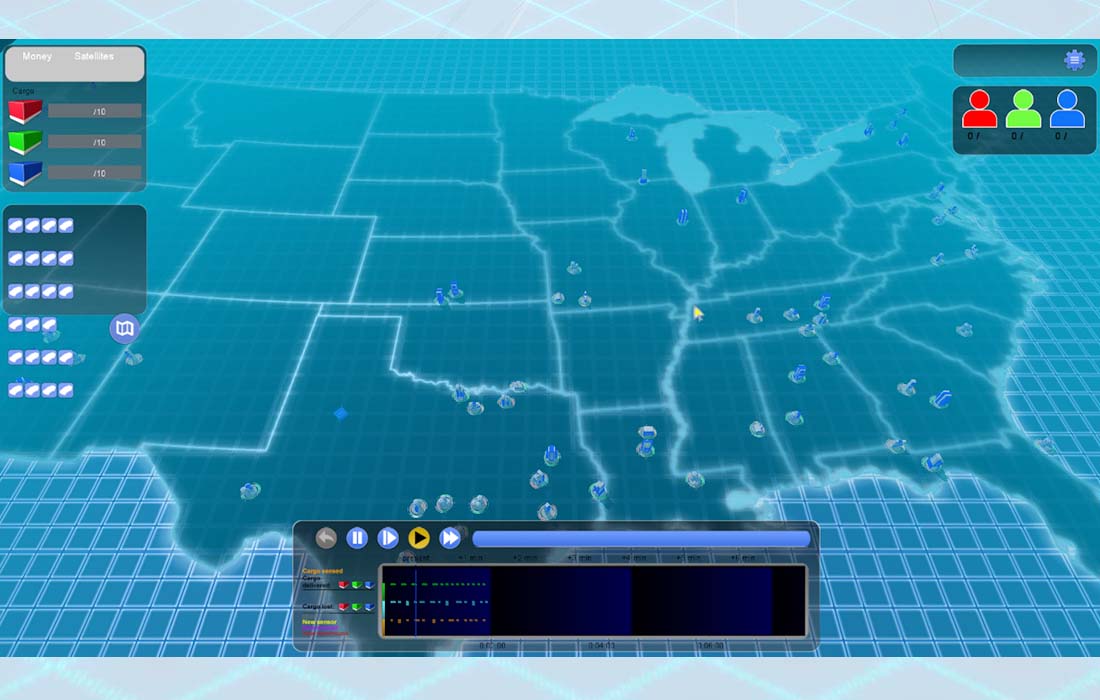
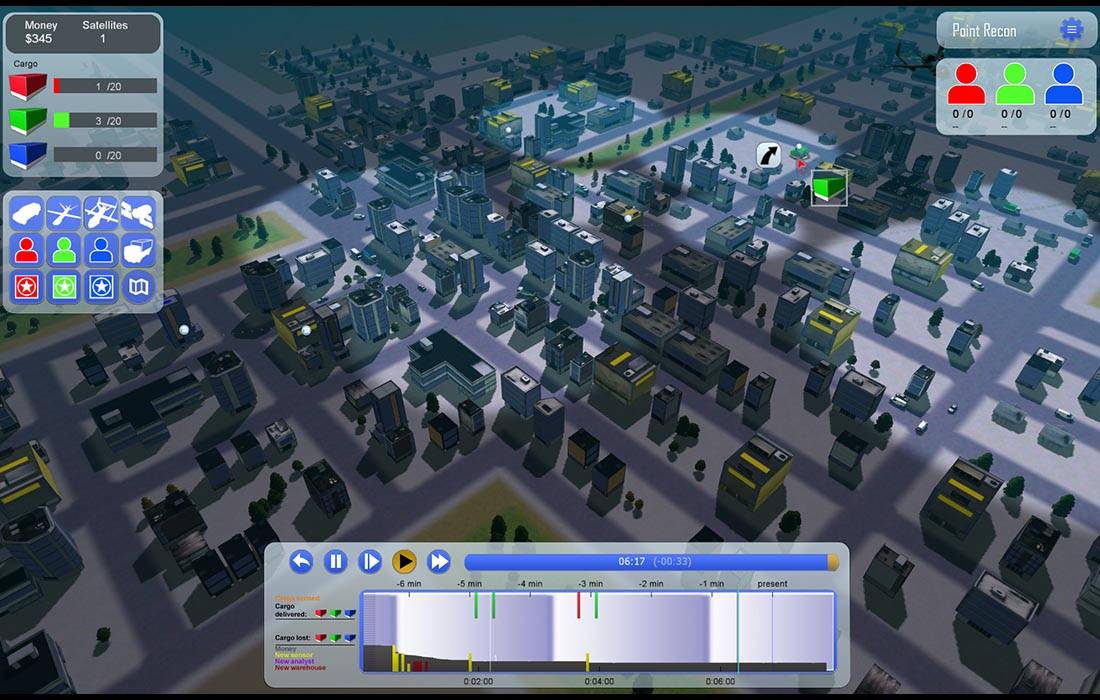
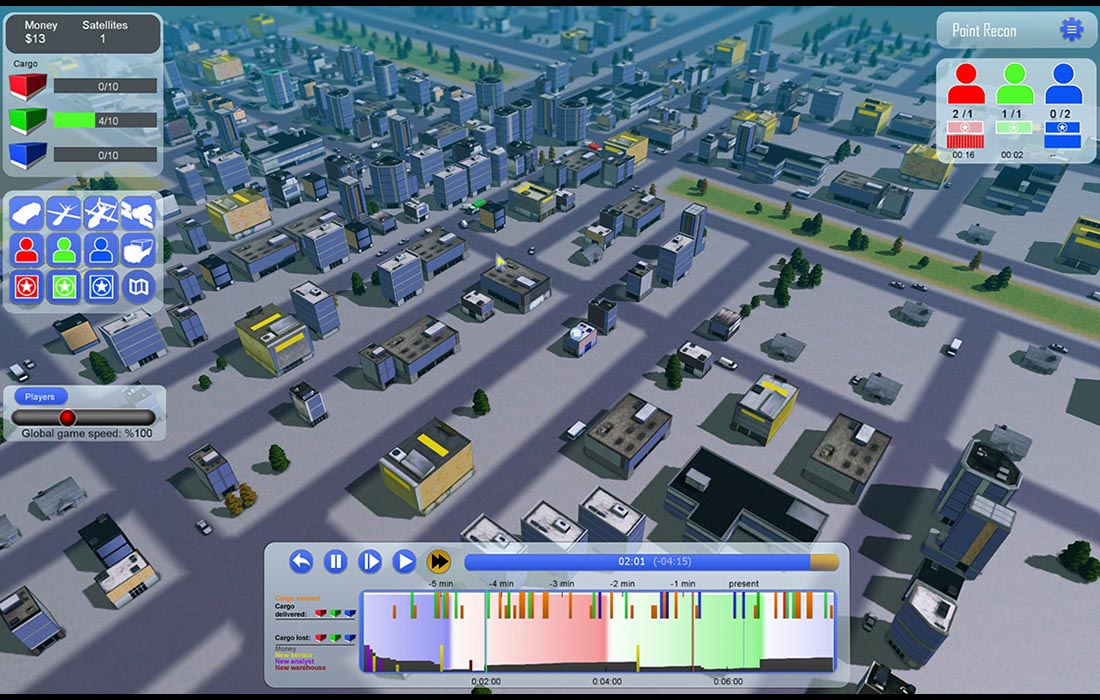
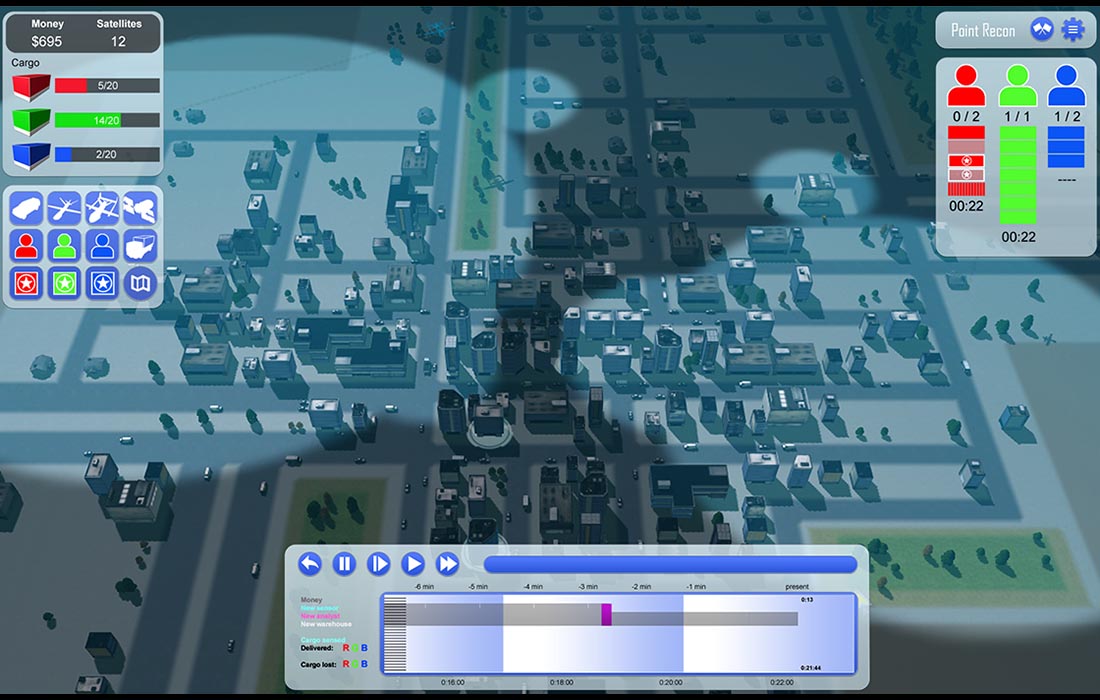
Improvised explosive devices (IEDs) can be very destructive to communities and soldiers. With Point Recon, the player learns different techniques to orchestrate reconaissance techniques in order to determine where IEDs are being built and deployed. Point Recon also has been built to interface with IBM process management software, demonstraiting a great real-world example of how process optimization engines can be integrated with serious games.
For more information on Point Recon, please contact info@www.hazardoussoftware.com.

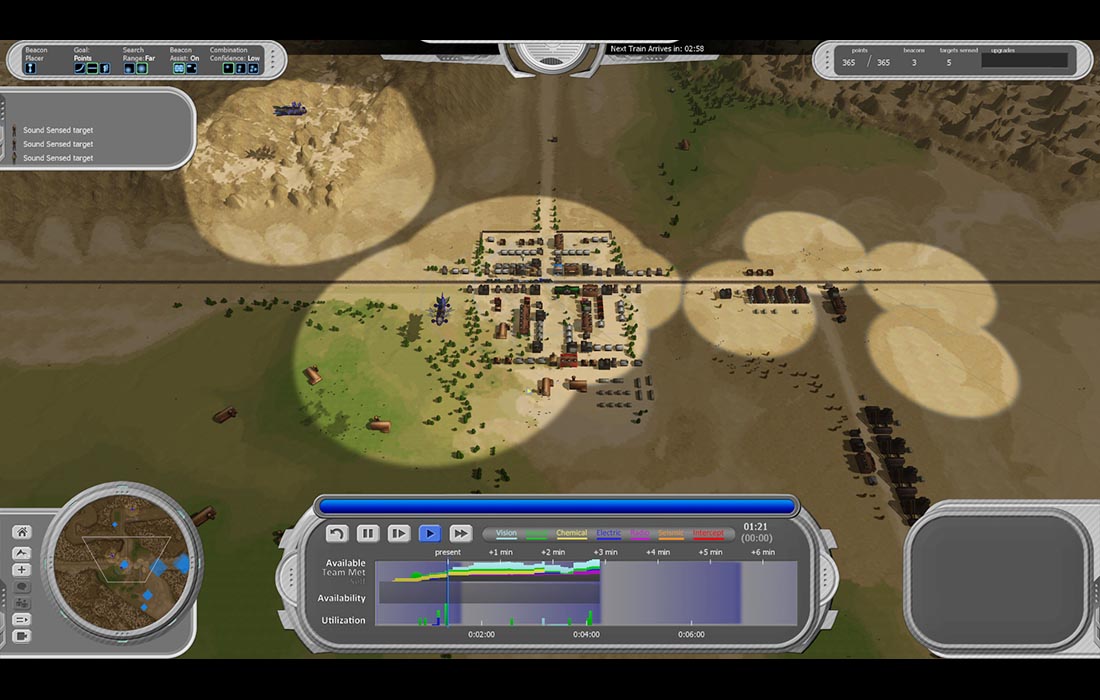
Imagine if in the late 1800’s, a company in the wild west started producing advancing technology rapidly, creating a steampunk world. Despite its rapid advancement, the company created deadly pollution and earthquakes, and began to infiltrate other companies. Playing as an investigative team, it is your job to determine what this company is up to, and whether the citizens of the town are in danger. SteamCraft is a fantastical model of a real-world problem that one of Hazardous Software’s client has faced, involving the investigation of dangerous environments. Players can use time manipulation to coordinate winning strategies.
For more information on SteamCraft, please contact info@www.hazardoussoftware.com.